Renowned security blogger Brian Krebs just gave us all a rare glimpse at the mess lurking under the rug in the world of cyber attackers. Krebs published a fairly detailed investigative report last week claiming he had found the author of the Mirai botnet – the person behind the screen name Anna Senpai.
The blogger was himself the victim of one of the largest DDoS attacks of 2016 when his blog Krebs On Security got hit with 620 gigabits of data per second in September. The attack used the Mirai botnet and it compelled Krebs to begin the four month hunt to uncover the malware’s main author.
Per the report, all trails lead to 20-year-old Rutgers University student, Paras Jha. Jha responded by denying the claim but he’s already been contacted by the FBI more than once regarding cyber attacks, reports nj.com.
Krebs also goes into detail about the interesting way the Mirai botnet evolved over time. It’s an origin story mixing the geek worlds of online gaming and anime-lore with traditional motivations of revenge, greed, and narcissism.
In its earliest days in 2014, Mirai started off targeting servers of the addictive online game Minecraft. “A large, successful Minecraft server with more than a thousand players logging on each day can easily earn the server’s owners upwards of $50,000 per month,” the blog explains. This makes them a lucrative target for attack because once the server goes down, impatient players will leave in droves to other servers not under attack.
As this was going on, Jha ran a one-man company protecting Minecraft server companies from attacks called ProTraf Solutions. In essence, Krebs claims he was attacking servers and competing security companies to generate more business for himself.
Krebs got himself tied up with Mirai when he ran a blog post in September with incriminating information about two hackers in Israel behind the ‘vDos’ attack service. Krebs claims angry vDos clients hired Anna Senpai to run a Mirai attack on the KrebsOnSecurity website as retaliation. Anna Senpai released Mirai’s source code to the public shortly thereafter in order to put it in the hands of more people and take some of the heat off them.
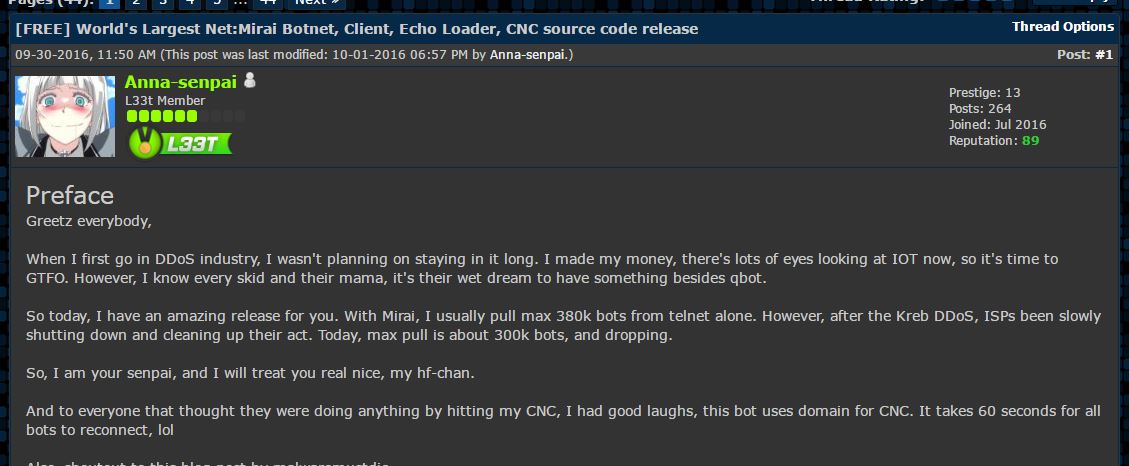
The FBI hasn’t officially responded to the report. But regardless of Anna Senpai’s real identity, the full story does expose the seedy dealings of hackers along with some of their petty motivations.
The Mirai botnet attacks were only able to get so large because they could enlist the help of unsecured IoT devices. If you want to avoid making your smart fridge an unwitting accomplice in the next attack, think about changing its default password and following some best practices published by the FTC on securing your device.











