The National Cybersecurity and Communications Integration Center (NCCIC) released an advisory on Friday alerting about a sophisticated hacking campaign. Alert TA17-117A was released as a medium risk. According the NCCIC, “A medium priority incident may affect public health or safety, national security, economic security, foreign relations, civil liberties, or public confidence.”
The campaign is targeting the Information Technology, Energy, Healthcare and Public Health, Communications, and Critical Manufacturing sectors. According to the advisory, the attacks date back to at least May of 2016. While their investigation is still preliminary, the reason for the advisory is to get the information out.
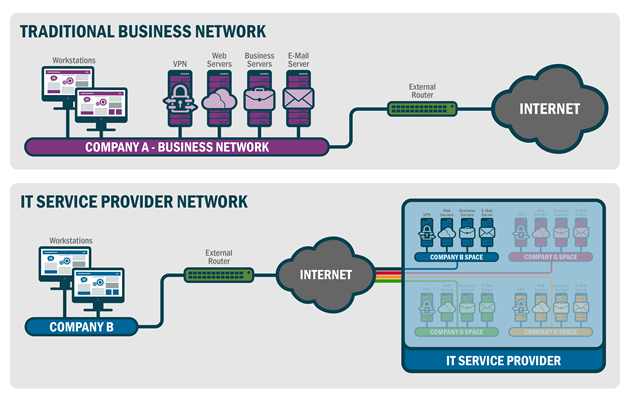
Early reports indicate that attackers are using stolen logins or certificates in order to gain entry into the target network. Once in, the attackers are then installing sophisticated malware to steal more user credentials. These credentials are then being used to navigate through the network. Particularly with IT Service Providers, their primary objective appears to be gaining access to customer environments.
IT Service Providers typically offer cloud based products for companies to host services like email and web hosting. A compromise here is very attractive to an attacker because this could lead to access to many companies at once. This is because “many IT service providers often leverage common core infrastructure that should be logically isolated to support multiple clients.”
During the analysis of several unnamed companies, NCCIC was able to determine how the attackers operated once they compromise a target. The advisory reports that the attackers will make “heavy use of PowerShell and the open source PowerSploit tool to enable assessment, reconnaissance, and lateral movement.”
While stealing credentials is the attackers primary objective, they are also installing malware on key target servers as well. Currently, they are using modified version of the PLUGX/SOGU and REDLEAVES malware. Of which, antivirus software is not currently able to detect some of the variants.
NCCIC has provided indicators of compromise (IOCs) for security departments to impliment. The hope here is for them to detect if they have been compromised. An IOC is security speak for: If these alarms go off, then you may have been hacked.
Of course, you should inform the authorities if you suspect a compromise. NCCIC recommends that organizations should implement a layered approach to security in order to defend from these or any type of attack.











