Researchers at CyberArk have discovered an odd behavior in the way Windows Defender scans files. CyberArc found that Defender can be bypassed when a user requests a file from a compromised SMB server. CyberArk’s Illusion Gap attack can effectively allow a malicious users to bypass the antivirus scanner. While CyberArk has yet to test this with other antivirus software, they suspect the issue “may possibly exist” with them as well.
How Illusion Gap is possible
CyberArk discovered two ways to bypass Windows Defender. Both methods to bypass Defender takes advantage of the API calls used by the software to request a file for scanning. Before we dive into the details, here is a brief rundown of how a Windows Defender scan works. Every time a file is requested from an SMB server, Defender requests the file first and will scan it. Once the scan is complete and the file is found to not be malicious the computer will then request and download the file.
In the first attack, the API call is different when Defender requests a file versus when the user request the file. Windows Defender uses the NtCreateFile(filename) while a standard user request uses NtCreateUserProcess(filename). This allows the server to recognize a request from Windows Defender.
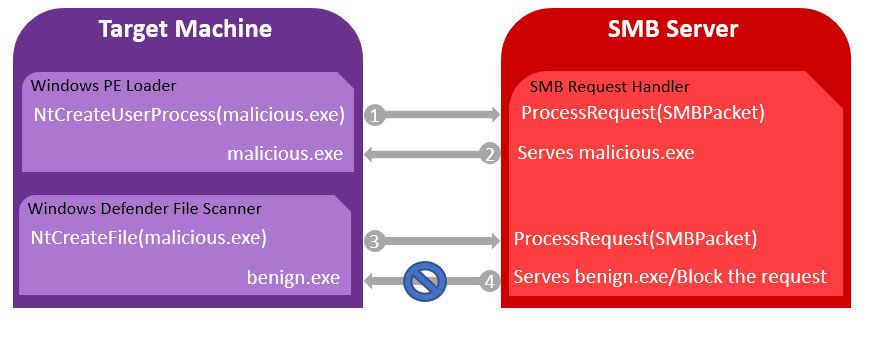
From Cyberark:
- First, the Windows PE Loader requests the file’s content to create the process.
- The SMB server identifies the request coming from Windows PE Loader and serves the malicious file.
- Windows Defender requests the file content to scan it.
- The SMB server identifies the request coming from Windows Defender and either serves a benign file or blocks the handle creation request.
Notice the two options that the SMB server can do with Defender’s request? For the second attack, If the malicious SMB server blocks the request then Defender will just “give up” and let the file run.
Microsoft’s response to Illusion Gap
CyberArk reached out to inform Microsoft of the attack. Microsoft responded that this does not seem to be a security flaw but a feature request.
“Thanks for your email. Based on your report, successful attack requires a user to run/trust content from an untrusted SMB share backed by a custom server that can change its behavior depending on the access pattern. This doesn’t seem to be a security issue but a feature request which I have forwarded to the engineering group.
Thanks again for reporting security issues to Microsoft responsibly and we appreciate your effort in doing so.”











